Azure Active Directory: 7 Powerful Insights You Must Know
Imagine managing thousands of users, apps, and devices across the globe with just a few clicks. That’s the power of Azure Active Directory. It’s not just a directory service—it’s the backbone of modern identity and access management in the cloud.
What Is Azure Active Directory and Why It Matters

Azure Active Directory (Azure AD) is Microsoft’s cloud-based identity and access management service. It helps employees sign in and access resources securely—whether they’re using Microsoft 365, the Azure portal, or thousands of SaaS applications like Salesforce, Dropbox, and Slack.
Core Definition and Functionality
Unlike traditional on-premises Active Directory, which relies on domain controllers and physical servers, Azure AD is built for the cloud. It manages user identities, authenticates logins, and authorizes access to resources across multiple platforms and devices.
- It supports single sign-on (SSO) for seamless access.
- It enables multi-factor authentication (MFA) for enhanced security.
- It integrates with on-premises directories via Azure AD Connect.
Azure AD is not a direct replacement for Windows Server Active Directory but rather a modern evolution designed for cloud-first environments. It uses REST APIs, OAuth 2.0, OpenID Connect, and SAML protocols to manage identity at scale.
Key Differences Between Azure AD and On-Premises AD
Understanding the distinction between Azure AD and traditional Active Directory is crucial for IT professionals planning hybrid or cloud-only deployments.
- Architecture: On-prem AD uses domain controllers in a hierarchical structure; Azure AD is a distributed, scalable cloud service.
- Protocols: On-prem AD relies on LDAP, Kerberos, and NTLM; Azure AD uses modern standards like OAuth and SAML.
- Management: On-prem AD is managed via Group Policy; Azure AD uses Conditional Access, Intune, and Identity Protection policies.
For organizations transitioning to the cloud, Azure AD offers greater flexibility, reduced infrastructure costs, and improved security posture. You can learn more about the architectural differences on Microsoft’s official documentation.
“Azure Active Directory is the identity backbone for the Microsoft cloud. It’s how users get access to applications, data, and services—securely and at scale.” — Microsoft Azure Documentation
Azure Active Directory Core Components Explained
To fully leverage Azure Active Directory, you must understand its foundational components. These building blocks enable identity management, access control, and security monitoring across your digital ecosystem.
Users, Groups, and Roles
At the heart of Azure AD are users, groups, and roles—each playing a critical role in access governance.
- Users: Represent individuals (employees, partners, customers) with unique identities. They can be cloud-only or synced from on-premises AD.
- Groups: Collections of users, devices, or other groups used to assign permissions and manage access efficiently.
- Roles: Define administrative privileges (e.g., Global Administrator, Helpdesk Admin) through Azure AD’s Role-Based Access Control (RBAC).
Role-based access ensures the principle of least privilege is maintained. For example, a billing clerk doesn’t need global admin rights—just access to the finance app. This minimizes risk and simplifies compliance.
Applications and Service Principals
Azure AD acts as an identity provider for applications. Every app registered in Azure AD has a corresponding service principal that defines its permissions and access scope.
- You can register custom apps or use pre-integrated SaaS apps from the Azure AD gallery.
- Service principals allow apps to authenticate and access resources without human intervention.
- App roles can be assigned to users or groups, enabling fine-grained access control.
For instance, when an employee logs into Salesforce via SSO, Azure AD validates their identity and passes a secure token to Salesforce. This process happens behind the scenes, improving both security and user experience. Explore the Microsoft guide on app objects for deeper technical insights.
Authentication Methods in Azure Active Directory
Authentication is the process of verifying user identity. Azure Active Directory supports a wide range of authentication methods, from simple passwords to passwordless experiences.
Password-Based Authentication
Despite the push toward passwordless solutions, passwords remain a common authentication method. Azure AD enhances password security with features like:
- Password hash synchronization from on-premises AD.
- Real-time password validation against banned password lists.
- Automatic detection of leaked credentials.
However, relying solely on passwords is risky. Phishing, brute force attacks, and credential stuffing make password-only systems vulnerable. That’s why Microsoft recommends enabling multi-factor authentication for all users.
Multi-Factor Authentication (MFA)
Azure AD Multi-Factor Authentication adds an extra layer of security by requiring two or more verification methods:
- Something you know (password).
- Something you have (phone, authenticator app, security key).
- Something you are (biometrics).
With MFA enabled, even if a password is compromised, an attacker cannot gain access without the second factor. According to Microsoft, MFA blocks over 99.9% of account compromise attacks.
You can enforce MFA through Conditional Access policies, which allow you to apply rules based on user, location, device, or risk level. Learn more about MFA setup at Microsoft’s MFA documentation.
Single Sign-On (SSO) with Azure Active Directory
Single sign-on is one of the most user-friendly and secure features of Azure Active Directory. It allows users to log in once and gain access to multiple applications without re-entering credentials.
How SSO Works in Azure AD
When a user attempts to access an application, Azure AD acts as the identity provider (IdP). It authenticates the user and sends a security token to the service provider (SP), such as Workday or Zoom.
azure active directory – Azure active directory menjadi aspek penting yang dibahas di sini.
- The token contains claims about the user (name, email, group membership).
- The application trusts Azure AD and grants access based on the token.
- No separate username/password is needed for the app.
This process uses standards like SAML, OAuth 2.0, and OpenID Connect. For example, SAML is commonly used for enterprise apps, while OAuth is preferred for mobile and web APIs.
Types of SSO Supported
Azure AD supports several SSO methods depending on the application type:
- Cloud SSO: For SaaS apps in the Azure AD app gallery (e.g., Dropbox, ServiceNow).
- Password Vaulting: Stores credentials securely and auto-fills them for legacy apps.
- Federated SSO: Uses federation protocols like SAML or WS-Fed with on-premises identity providers.
- Integrated Windows Authentication (IWA): Enables seamless access for domain-joined devices.
Organizations can configure SSO via the Azure portal with minimal coding. Microsoft provides step-by-step guides for over 2,600 pre-integrated apps, making deployment fast and reliable.
“Single sign-on reduces password fatigue and improves productivity by up to 40%.” — Gartner Research
Conditional Access and Security Policies in Azure Active Directory
Conditional Access is one of the most powerful security features in Azure Active Directory. It allows organizations to enforce access controls based on specific conditions, such as user location, device compliance, or sign-in risk.
Building Blocks of Conditional Access
A Conditional Access policy consists of three main components:
- Users and Groups: Who the policy applies to.
- Conditions: When the policy is triggered (e.g., user location, device platform, sign-in risk).
- Access Controls: What happens when the policy is triggered (e.g., require MFA, block access, require compliant device).
For example, you can create a policy that requires MFA for all users accessing email from outside the corporate network. Or, you can block access from unmanaged devices trying to reach sensitive financial systems.
These policies are enforced in real time and integrate with other Microsoft security tools like Azure AD Identity Protection and Microsoft Intune.
Real-World Use Cases
Organizations use Conditional Access to address common security challenges:
- Remote Workforce Security: Require MFA and compliant devices for employees working from home.
- Third-Party Access: Restrict contractors to specific apps and time windows.
- High-Risk Sign-Ins: Automatically block or challenge logins detected as risky by AI-driven analysis.
According to Microsoft, companies using Conditional Access see a 67% reduction in identity-related breaches. Explore policy creation in the official Conditional Access documentation.
Identity Protection and Risk Detection in Azure Active Directory
In today’s threat landscape, proactive identity protection is essential. Azure AD Identity Protection uses machine learning and risk-based policies to detect and respond to suspicious activities.
Understanding Risk Detections
Azure AD monitors sign-in attempts and user behavior to identify potential threats. It classifies risks into two categories:
- Sign-in Risk: Likelihood that a sign-in attempt is not from the legitimate user (e.g., anonymous IP, unfamiliar location).
- User Risk: Likelihood that a user account is compromised (e.g., leaked credentials, malware infection).
Risk levels are categorized as low, medium, or high. Based on the risk level, Azure AD can trigger automated responses like requiring MFA, forcing a password reset, or blocking access.
Automated Remediation with Risk Policies
You can configure risk-based policies to automatically respond to detected threats:
- Require MFA for medium sign-in risk.
- Require password reset for high user risk.
- Block access for impossible travel or anonymous IP addresses.
These policies reduce the burden on IT teams and ensure rapid response to threats. For example, if a user’s credentials appear in a dark web leak, Azure AD can flag the account and enforce a password reset before any damage occurs.
Identity Protection is available in Azure AD Premium P2 and integrates with Microsoft Defender for Cloud Apps for deeper visibility. Read more at Microsoft’s Identity Protection guide.
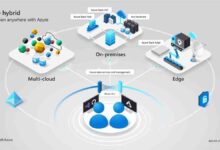
Hybrid Identity: Bridging On-Premises and Cloud with Azure AD
Most enterprises don’t operate in a purely cloud or on-premises environment—they use a hybrid model. Azure Active Directory supports seamless integration between on-premises Active Directory and the cloud.
Azure AD Connect: The Bridge to the Cloud
Azure AD Connect is the primary tool for synchronizing identities from on-premises AD to Azure AD. It enables:
- Password hash synchronization.
- Pass-through authentication.
- Federation with AD FS.
- Group and device synchronization.
By using Azure AD Connect, organizations can maintain a single source of truth for user identities while enabling cloud-based access and security features. It’s a critical component for hybrid identity management.
Authentication Methods in Hybrid Environments
In a hybrid setup, users can authenticate in several ways:
azure active directory – Azure active directory menjadi aspek penting yang dibahas di sini.
- Password Hash Sync (PHS): Password hashes are synced to Azure AD; authentication occurs in the cloud.
- Pass-Through Authentication (PTA): Authentication requests are validated against on-premises domain controllers in real time.
- Federation (AD FS): Uses on-premises AD FS servers to issue tokens for cloud access.
PTA is often preferred for its simplicity and reliability, while federation offers more control for organizations with strict compliance requirements. Microsoft recommends PHS or PTA over AD FS for new deployments due to lower complexity and better cloud integration.
For detailed deployment guidance, visit Microsoft’s Azure AD Connect documentation.
Advanced Features: Privileged Identity Management and B2B/B2C
Beyond basic identity management, Azure Active Directory offers advanced capabilities for securing privileged access and extending identity to external users.
Privileged Identity Management (PIM)
Privileged accounts are high-value targets for attackers. Azure AD Privileged Identity Management (PIM) helps secure these accounts by enabling just-in-time (JIT) and time-bound access.
- Administrators don’t have permanent elevated rights.
- They must activate their role when needed, often with MFA approval.
- Access is automatically deactivated after a set period.
PIM also provides audit logs and approval workflows, enhancing accountability and compliance. It’s essential for meeting regulatory standards like GDPR, HIPAA, and SOC 2.
Azure AD B2B and B2C Collaboration
Azure AD supports two external identity models:
- B2B (Business-to-Business): Invite external users (partners, vendors) to access your apps securely. They use their own organizational credentials.
- B2C (Business-to-Consumer): Create customer-facing apps with custom sign-up and sign-in experiences (e.g., retail portals, mobile apps).
B2B simplifies collaboration without creating guest accounts manually. B2C allows brands to manage millions of consumer identities with scalable, customizable authentication flows. Both are critical for modern digital business strategies.
Learn more about B2B collaboration at Microsoft’s B2B guide and B2C at Azure AD B2C documentation.
What is Azure Active Directory used for?
Azure Active Directory is used for managing user identities, enabling single sign-on, enforcing security policies, and providing secure access to cloud and on-premises applications. It’s the foundation of identity and access management in Microsoft’s cloud ecosystem.
Is Azure AD the same as Windows Active Directory?
No, Azure AD is not the same as Windows Server Active Directory. While both manage identities, Azure AD is cloud-based, uses modern authentication protocols, and is designed for SaaS and cloud applications, whereas on-prem AD is directory-based, uses LDAP/Kerberos, and is optimized for Windows networks.
How do I enable multi-factor authentication in Azure AD?
You can enable MFA in Azure AD by navigating to the Azure portal, selecting Azure Active Directory, then going to Security > Multi-Factor Authentication. From there, you can enable MFA for individual users or use Conditional Access policies to enforce it organization-wide.
What is the difference between Azure AD Free and Premium?
Azure AD Free includes basic identity and SSO features. Premium P1 adds Conditional Access, hybrid identity, and self-service password reset. Premium P2 includes Identity Protection, Privileged Identity Management, and advanced risk detection.
Can Azure AD replace on-premises Active Directory?
Azure AD can partially replace on-premises AD, especially for cloud-first organizations. However, many enterprises use a hybrid model. For full replacement, features like Group Policy and legacy app dependencies must be addressed through alternatives like Intune and modern app deployment.
In conclusion, Azure Active Directory is far more than a cloud directory—it’s a comprehensive identity and access management platform that empowers secure, seamless access across modern digital environments. From single sign-on and multi-factor authentication to Conditional Access and identity protection, Azure AD provides the tools organizations need to defend against evolving cyber threats while enabling productivity. Whether you’re managing internal employees, external partners, or millions of customers, Azure AD scales with your needs and integrates deeply with the Microsoft ecosystem. As the world moves further into cloud and hybrid work models, mastering Azure Active Directory isn’t just an IT advantage—it’s a business imperative.
azure active directory – Azure active directory menjadi aspek penting yang dibahas di sini.
Recommended for you 👇
Further Reading: