Windows Azure AD: 7 Powerful Features You Must Know
Windows Azure AD isn’t just another cloud tool—it’s the backbone of modern identity management. Whether you’re securing remote teams or streamlining access across apps, this platform delivers unmatched control and scalability with a seamless user experience.
What Is Windows Azure AD and Why It Matters

Windows Azure AD, more formally known as Microsoft Entra ID (formerly Azure Active Directory), is Microsoft’s cloud-based identity and access management service. It enables organizations to securely manage user identities, control access to applications, and enforce policies across hybrid and cloud environments. Unlike traditional on-premises Active Directory, Windows Azure AD is built for the cloud-first world, supporting modern authentication protocols like OAuth 2.0, OpenID Connect, and SAML.
Core Purpose of Windows Azure AD
The primary goal of Windows Azure AD is to provide a centralized identity system that connects users to the resources they need—whether those are Microsoft 365, Azure, or thousands of third-party SaaS applications. It acts as a digital gatekeeper, ensuring only authorized individuals can access specific data and tools.
- Centralized user identity management
- Single Sign-On (SSO) across cloud and on-premises apps
- Integration with Microsoft 365, Azure, and thousands of SaaS platforms
According to Microsoft, over 1.4 billion identities are managed through Azure AD daily, making it one of the most widely used identity platforms globally. This scale underscores its reliability and enterprise-grade security.
How Windows Azure AD Differs from On-Premises AD
While both systems manage user identities, Windows Azure AD is fundamentally different from traditional Active Directory. On-premises AD relies on domain controllers, Group Policy Objects (GPOs), and LDAP protocols, which are designed for local network environments. In contrast, Windows Azure AD uses REST APIs, JSON, and modern authentication standards to support distributed, mobile, and cloud-centric workforces.
- On-prem AD uses Kerberos and NTLM; Azure AD uses OAuth and OpenID Connect
- Azure AD supports multi-factor authentication (MFA) natively; on-prem requires add-ons
- Azure AD enables self-service password reset and conditional access policies
“Azure AD is not a cloud version of Active Directory—it’s a new identity platform designed for the cloud era.” — Microsoft Documentation
Key Features of Windows Azure AD
Windows Azure AD offers a robust suite of features that empower organizations to manage identities efficiently and securely. These capabilities go beyond simple login systems, providing intelligent access control, automation, and deep integration with Microsoft’s ecosystem.
Single Sign-On (SSO) Across Applications
One of the most impactful features of Windows Azure AD is its ability to provide seamless Single Sign-On to thousands of cloud applications. Users can log in once and gain access to all their authorized apps without re-entering credentials.
- Supports over 2,600 pre-integrated SaaS apps like Salesforce, Dropbox, and Zoom
- Enables password-less access through Windows Hello or FIDO2 security keys
- Reduces password fatigue and improves productivity
For example, a marketing team using Adobe Creative Cloud, HubSpot, and Microsoft Teams can access all three with a single login via Windows Azure AD. This integration is achieved through SAML or OIDC protocols, which securely transmit identity information between the app and Azure AD.
Learn more about app integration: Microsoft Azure AD App Integration Guide
Multi-Factor Authentication (MFA)
Security is paramount in today’s threat landscape, and Windows Azure AD delivers strong protection through Multi-Factor Authentication. MFA requires users to verify their identity using at least two methods—something they know (password), something they have (phone or token), or something they are (biometrics).
- Available via phone call, text message, Microsoft Authenticator app, or hardware tokens
- Can be enforced based on user risk, location, or device compliance
- Reduces account compromise by up to 99.9% according to Microsoft’s security research
Organizations can configure MFA policies to trigger under specific conditions. For instance, if a user logs in from an unfamiliar country, Azure AD can automatically prompt for MFA, adding an extra layer of security.
Conditional Access Policies
Conditional Access is a powerful feature within Windows Azure AD that allows administrators to define access rules based on real-time signals such as user location, device health, sign-in risk, and application sensitivity.
- Create policies like “Block access from outside the corporate network”
- Require compliant devices (e.g., Intune-managed) for accessing sensitive data
- Enforce MFA for high-risk sign-ins detected by Identity Protection
For example, a financial institution might set a policy that blocks access to its internal banking portal unless the user is on a company-managed device and located within the country. This dynamic control ensures that access is granted only when it’s safe to do so.
Identity and Access Management with Windows Azure AD
Effective identity management is the cornerstone of cybersecurity, and Windows Azure AD provides comprehensive tools to manage who can access what, when, and under what conditions.
User Lifecycle Management
From onboarding to offboarding, Windows Azure AD streamlines the entire user lifecycle. Administrators can automate provisioning and deprovisioning of user accounts across multiple applications using SCIM (System for Cross-domain Identity Management).
- Automatically create user accounts when hired
- Assign role-based access based on job function
- Revoke access instantly upon termination
This automation reduces administrative overhead and minimizes the risk of orphaned accounts, which are a common security vulnerability.
Role-Based Access Control (RBAC)
Windows Azure AD supports Role-Based Access Control, allowing organizations to assign permissions based on job roles rather than individual users. This principle of least privilege ensures users only have access to the resources necessary for their role.
- Predefined roles like Global Administrator, User Administrator, and Billing Administrator
- Custom roles can be created for granular control
- Role assignments can be reviewed and audited regularly
For instance, an HR manager might have access to employee records in Azure AD but not to financial systems, while a finance analyst has access to budgeting tools but not personnel data.
Access Reviews and Governance
To maintain compliance and reduce access sprawl, Windows Azure AD offers Access Reviews—a feature that enables periodic review of user permissions. Managers can approve or revoke access to groups, apps, or roles on a scheduled basis.
- Schedule quarterly reviews for sensitive applications
- Automate revocation of unused access
- Generate audit reports for compliance (e.g., GDPR, HIPAA)
This proactive governance helps organizations meet regulatory requirements and maintain a clean, secure access model.
Security and Threat Protection in Windows Azure AD
With cyber threats evolving rapidly, Windows Azure AD integrates advanced security capabilities to detect, prevent, and respond to identity-based attacks.
Azure AD Identity Protection
Identity Protection uses machine learning and risk detection to identify suspicious sign-in activities and compromised accounts. It analyzes factors like IP reputation, device health, and user behavior to assign a risk level to each login attempt.
- Detects anomalies such as sign-ins from unfamiliar locations
- Flags leaked credentials found on the dark web
- Automatically blocks or challenges high-risk sign-ins
For example, if a user’s credentials are exposed in a data breach, Identity Protection can detect usage of those credentials from a new device and prompt for MFA or block access entirely.
Explore more: Azure AD Identity Protection Overview
Risk-Based Conditional Access
Building on Conditional Access, risk-based policies allow organizations to respond dynamically to threat levels. Instead of applying blanket rules, policies can be triggered based on real-time risk scores.
- Low risk: Allow access with standard authentication
- Medium risk: Require MFA
- High risk: Block access or require device compliance
This adaptive approach balances security and usability, ensuring users aren’t unnecessarily blocked while still protecting against threats.
Privileged Identity Management (PIM)
For users with elevated permissions—like administrators—Windows Azure AD offers Privileged Identity Management (PIM). PIM enables just-in-time (JIT) access, meaning privileges are granted only when needed and for a limited time.
- Reduce standing admin privileges
- Audit all privileged activities
- Require approval for elevation requests
This minimizes the attack surface and ensures that even powerful accounts are not constantly exposed.
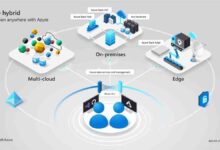
Integration and Hybrid Capabilities of Windows Azure AD
Many organizations operate in hybrid environments, with some resources on-premises and others in the cloud. Windows Azure AD excels in bridging these worlds through seamless integration tools.
Azure AD Connect
Azure AD Connect is the primary tool for synchronizing on-premises Active Directory with Windows Azure AD. It enables password hash synchronization, pass-through authentication, and federation with AD FS.
- Synchronize user accounts, groups, and passwords
- Supports seamless SSO for hybrid users
- Can be deployed on-premises with minimal configuration
For example, a company with legacy ERP systems on-premises can still allow employees to use their corporate credentials to access cloud apps via Azure AD Connect.
Official guide: Azure AD Connect Installation Guide
Hybrid Identity Scenarios
Windows Azure AD supports various hybrid identity models, allowing organizations to choose the best fit for their infrastructure.
- Password Hash Synchronization (PHS): Sync password hashes to Azure AD
- Pass-Through Authentication (PTA): Validate passwords against on-prem AD in real time
- Federation (AD FS): Use existing federation infrastructure for SSO
Each model has trade-offs in terms of complexity, latency, and dependency on on-prem systems. PTA is often preferred for its simplicity and real-time validation.
Integration with Microsoft 365 and Azure
Windows Azure AD is deeply integrated with Microsoft 365 and Azure, serving as the identity backbone for both platforms.
- Microsoft 365 uses Azure AD for user authentication and licensing
- Azure relies on Azure AD for role-based access to cloud resources
- Unified audit logs across M365 and Azure for compliance
This tight integration ensures consistent security policies and simplifies administration across Microsoft’s ecosystem.
Best Practices for Deploying Windows Azure AD
Successfully implementing Windows Azure AD requires careful planning and adherence to security and operational best practices.
Start with a Clear Identity Strategy
Before deploying, organizations should define their identity model: cloud-only, hybrid, or federation. This decision impacts authentication methods, user experience, and administrative overhead.
- Assess current AD structure and user distribution
- Define authentication method (PHS, PTA, or AD FS)
- Plan for coexistence during migration
A phased rollout is recommended, starting with pilot groups before full deployment.
Enforce Multi-Factor Authentication
MFA should be mandatory for all users, especially administrators. It’s one of the most effective ways to prevent unauthorized access.
- Enable MFA for all global and privileged admins
- Use the Microsoft Authenticator app for push notifications
- Provide user training to reduce friction
According to Microsoft, accounts with MFA enabled are 99.9% less likely to be compromised.
Implement Conditional Access Policies
Use Conditional Access to enforce security policies based on context. Start with basic rules like requiring MFA for external access, then expand to risk-based policies.
- Block legacy authentication protocols (e.g., IMAP, SMTP)
- Require compliant devices for accessing sensitive apps
- Monitor policy impact using sign-in logs
Regularly review and refine policies to adapt to changing business needs.
Future of Identity: Windows Azure AD and Beyond
As digital transformation accelerates, the role of identity management is becoming more strategic. Windows Azure AD is evolving to meet emerging challenges like zero trust, passwordless authentication, and AI-driven security.
Towards a Passwordless Future
Microsoft is actively promoting a passwordless future through Windows Azure AD. Features like Windows Hello, FIDO2 security keys, and the Microsoft Authenticator app allow users to log in without passwords.
- Eliminates risks associated with weak or reused passwords
- Improves user experience with biometric or device-based authentication
- Supports phishing-resistant authentication methods
Organizations can gradually transition users to passwordless sign-in, starting with pilot groups and expanding over time.
Zero Trust Architecture Integration
Windows Azure AD is a foundational component of Microsoft’s Zero Trust model, which operates on the principle of “never trust, always verify.”
- Every access request is authenticated and authorized
- Access is granted based on device health, user identity, and context
- Continuous monitoring and validation throughout the session
By integrating Azure AD with Intune, Conditional Access, and Microsoft Defender, organizations can build a comprehensive Zero Trust framework.
AI and Machine Learning in Identity Security
Future enhancements in Windows Azure AD will leverage AI to improve threat detection and automate responses. Machine learning models will become more accurate in identifying anomalous behavior and predicting potential breaches.
- Proactive risk scoring based on behavioral analytics
- Automated remediation of compromised accounts
- Personalized security recommendations for administrators
These advancements will make identity security more intelligent and adaptive.
What is Windows Azure AD used for?
Windows Azure AD is used for managing user identities, enabling single sign-on to cloud and on-premises applications, enforcing security policies, and protecting against identity-based threats. It serves as the central identity provider for Microsoft 365, Azure, and thousands of third-party apps.
How does Windows Azure AD differ from traditional Active Directory?
Traditional Active Directory is designed for on-premises networks using protocols like LDAP and Kerberos, while Windows Azure AD is cloud-native, using modern standards like OAuth and OpenID Connect. Azure AD supports mobile, remote, and hybrid workforces with built-in MFA, conditional access, and SaaS app integration.
Can Windows Azure AD be used in hybrid environments?
Yes, Windows Azure AD supports hybrid environments through Azure AD Connect, which synchronizes on-premises Active Directory with the cloud. It enables seamless authentication and access control across both on-prem and cloud resources.
Is Multi-Factor Authentication mandatory in Windows Azure AD?
While not mandatory by default, Microsoft strongly recommends enabling MFA for all users, especially administrators. MFA significantly reduces the risk of account compromise and is a best practice for securing cloud identities.
What is the future of Windows Azure AD?
The future of Windows Azure AD includes a shift toward passwordless authentication, deeper integration with Zero Trust security models, and enhanced AI-driven threat detection. Microsoft continues to evolve the platform to meet the demands of modern, distributed workforces.
Windows Azure AD has transformed how organizations manage digital identities in the cloud era. From robust security features like MFA and Conditional Access to seamless integration with Microsoft 365 and hybrid environments, it offers a comprehensive solution for modern identity management. As cyber threats grow more sophisticated, the platform’s evolution toward passwordless authentication and AI-powered protection ensures it remains at the forefront of enterprise security. By adopting best practices and leveraging its full capabilities, businesses can build a secure, scalable, and user-friendly identity foundation for the future.
Recommended for you 👇
Further Reading: